You are not logged in.
- Topics: Active | Unanswered
Pages: 1
#1 2020-08-10 17:12:10
- Vernon
- Member
- Registered: 2020-07-19
- Posts: 89
HOWTO: Firefox DoH (DNS over HTTPS)
Firefox now offers DoH (DNS over HTTPS which promises a simple way to protect yourself against DNS poisoning. DoH can be enabled through the Firefox Edit->Prefereces->General->Network Settings menu.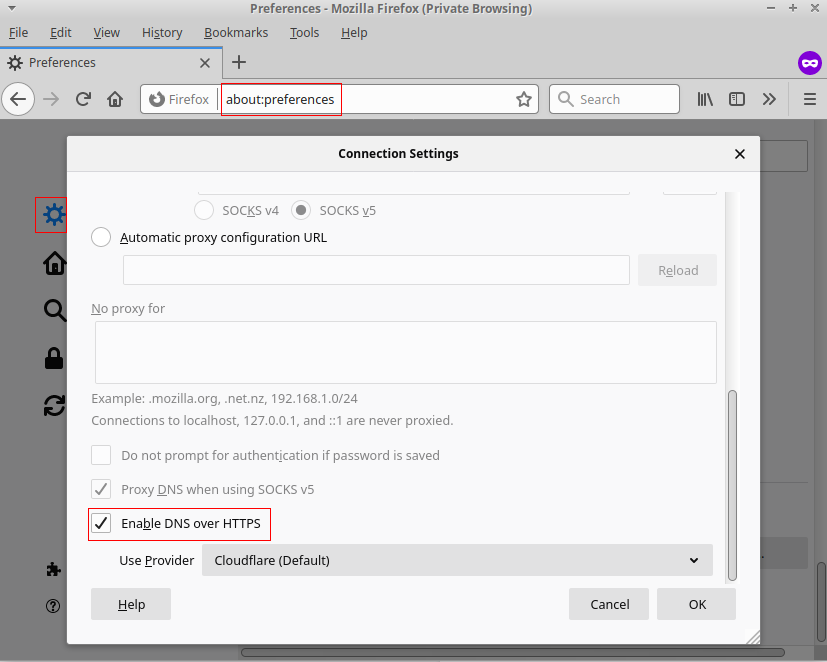
However, by default, Firefox sets DoH to TRR=2. This means that if the DoH host is unreachable or returns NXDOMAIN, Firefox will silently failover to the local, possibly poisoned DNS.
In order to ensure that Firefox always uses DoH and never fails over to the local DNS, go into the about:config settings and change network.trr.mode from 2 to 3,.

With network.trr.mode set to 3, Firefox will. display message Hmm. We’re having trouble finding that site whenever the DoH host is unreachable or returns NXDOMAIN.
More information is at
https://bugzilla.mozilla.org/show_bug.cgi?id=1656895
Last edited by Vernon (2020-08-10 21:16:37)
Offline
#2 2020-08-11 08:07:23
- yeti
- Member

- From: *** GONE ***
- Registered: 2017-02-23
- Posts: 370
Re: HOWTO: Firefox DoH (DNS over HTTPS)
Why should I trust Cloudflare more than other DNSs?
Offline
#3 2020-08-11 14:16:50
- Vernon
- Member
- Registered: 2020-07-19
- Posts: 89
Re: HOWTO: Firefox DoH (DNS over HTTPS)
Why should I trust Cloudflare more than other DNSs?
Depends what you mean by trust.
Do you trust your dog not to rip out your throat when when you sleep? Hopefully yes.
Do you trust your dog to not steal food when you are not looking? Maybe not.
Similarly, can you trust Cloudflare to return the correct IP address when you browse to https://www.deutsche-bank.de/ and not send you to a malicious, cloned web site? Yes.
Can you trust Cloudflare not to track your DNS lookups? Probably not.
It is very easy for a malicious hotspot operator to spoof DNS lookups. I once ran a non-malicious captive portal where the DNS was configured so whatever web address a user typed in, it would resolve to the captive portal web server. I stopped doing this because so many devices cache DNS lookups these days, users would have to reboot their devices in order to restore correct DNS lookups. Firefox DNS over HTTPS immunizes you against DNS spoofing.
Offline
#4 2020-08-11 16:32:26
- Head_on_a_Stick
- Member

- From: London
- Registered: 2019-03-24
- Posts: 3,125
- Website
Re: HOWTO: Firefox DoH (DNS over HTTPS)
Other providers can be used instead of CloudFlare: https://support.mozilla.org/en-US/kb/fi … -providers
DoH is not without it's criticisms: https://www.zdnet.com/article/dns-over- … perts-say/
Brianna Ghey — Rest In Power
Offline
#5 2020-08-11 17:02:30
- golinux
- Administrator

- Registered: 2016-11-25
- Posts: 3,662
Re: HOWTO: Firefox DoH (DNS over HTTPS)
Doesn't running unbound get rid of cloudflare?
Offline
#6 2020-08-11 17:11:37
- Head_on_a_Stick
- Member

- From: London
- Registered: 2019-03-24
- Posts: 3,125
- Website
Re: HOWTO: Firefox DoH (DNS over HTTPS)
DoH would bypass unbound.
Brianna Ghey — Rest In Power
Offline
#7 2020-08-11 20:49:34
- Marjorie
- Member
- From: Teignmouth, UK
- Registered: 2019-06-09
- Posts: 222
Re: HOWTO: Firefox DoH (DNS over HTTPS)
My own choice is to use dnscrypt-proxy, which:
1) Gives you a wide choice of DNS provider, including Cloudflare, using either DoH or Dnscrypt. You can choose from a large number of non-logging (or at least services that say they are) and/or DNSSEC and/or filtered/non-filtered DNS providers.
2) You get periodically to randomise your DNS provider, so no one service sees it all.
3) You will usually choose nearer DNS providers with a lower RTT than Cloudflare (at least here where Ii am in the UK).
4) You can cache your queries, reducing what hits your provider and proving near-instant lookups on your most used sites.
5) You can select from multiple blocklists.
6) it works for all your internet traffic, not just your browser. On mine I also provide a DNS service for other nodes on my network.
7) In the latest versions you can set up a (set of) DNS relays between you and the DNS provider, which masks your IP from them and your query form the relays.
In Firefox (about:config) you set your Network.TRR.mode to 5, so bypass the internal DoH with /etc/resolv.conf pointing to your dnscrypt-proxy. There is also an option that allows you to provide a DoH server for Firefox, which then connects to the internet using any of the other dnscrypt-proxy options.
Last edited by Marjorie (2020-08-11 20:50:54)
Offline
#8 2020-08-11 21:57:58
- Vernon
- Member
- Registered: 2020-07-19
- Posts: 89
Re: HOWTO: Firefox DoH (DNS over HTTPS)
...
DoH is not without it's criticisms: https://www.zdnet.com/article/dns-over- … perts-say/
Thanks for this link. Although I disagree with the validity of every point except the first one. DoH doesn't actually prevent ISPs user tracking, I provided this link to Firefox since they seem to be confused about what protections DoH provides as well.
https://bugzilla.mozilla.org/show_bug.cgi?id=1610365
My comments follow:
DoH doesn't actually prevent ISPs user tracking
Correct. But that is not the purpose of DoH. DoH strictly provides immunity from DNS spoofing. It's just like criticizing Firefox privacy mode for not preventing ISP tracking.
DoH bypasses enterprise policies
Yes, you will have to do a little more work to block by IP address. Too bad
DoH weakens cyber-security
Translation: DoH makes my spying more difficult
DoH also bypasses legitimate blocklists, not just censorship
This smuggles in the notion that there are legitimate block lists. This is just someone who is disappointed that DoH makes Internet censorship slightly more difficult
DoH shouldn't be recommended to dissidents
Just repeating the first point that DoH does not provide anonymity. This is just like saying that dissidents shouldn't use privacy mode because it doesn't provide anonymity either
DoH centralizes DNS traffic at a few DoH resolvers
DNS traffic is already centralized amongst a few ISP resolvers.
Offline
#9 2020-08-12 03:58:44
- Vernon
- Member
- Registered: 2020-07-19
- Posts: 89
Re: HOWTO: Firefox DoH (DNS over HTTPS)
My own choice is to use dnscrypt-proxy.
...
Thanks for this info. I did not know about dnscrypt-proxy. You may be surprised to learn that I do not use DoH either. I just became interested in DoH when Fedora stated that they may enable DNS over TLS by default.
At home, I run my own DNS server. It is not internet facing. Debian used to, and I assume that they still do give you a fully functioning DNS server with no configuration necessary simply by typing apt-get install bind9. The Fedora package manager for bind did a better job because Fedora would update your roots file for you. Whereas, with Debian, you at least used to have to grab an update from ftp.internic.net .
Remotely, if I am concerned about DNS spoofing or other chicanery, I OpenVPN into my home OpenVPN server. My .ovpn file is configured so that I will use my home DNS and not the DNS at my remote location.
If I am concerned about anonymity, I openvpn into free VPN provider freevpn.me or vpnbook. I modify their provided .ovpn files to ensure that I am using their DNS server instead of my own.
If I desire even more anonymity, there is always I2P or freenet
Offline
#10 2020-08-12 16:40:13
- Head_on_a_Stick
- Member

- From: London
- Registered: 2019-03-24
- Posts: 3,125
- Website
Re: HOWTO: Firefox DoH (DNS over HTTPS)
I really don't understand what DoH offers that cannot be bettered with
# echo 'nameserver 9.9.9.9' > /etc/resolv.conf
# chattr +i /etc/resolv.conf^ That will work for network activity that doesn't involve a browser, unlike DoH.
And there is also https://pkginfo.devuan.org/stage/beowul … ack-3.html
Last edited by Head_on_a_Stick (2020-08-12 16:41:28)
Brianna Ghey — Rest In Power
Offline
#11 2020-08-13 00:13:01
- Vernon
- Member
- Registered: 2020-07-19
- Posts: 89
Re: HOWTO: Firefox DoH (DNS over HTTPS)
I really don't understand what DoH offers that cannot be bettered with
# echo 'nameserver 9.9.9.9' > /etc/resolv.conf # chattr +i /etc/resolv.conf^ That will work for network activity that doesn't involve a browser, unlike DoH.
...
The short answer is that if you do that, you will be unable to do any local LAN-only domain DNS lookups. Firefox DoH allows a user to easily protect themselves when traveling from DNS poisoning while still allowing for local LAN-only DNS lookups when they return home with a one time Firefox configuration change. And as a Devuan user, you are fortunate in that your version of Firefox implements DoH correctly whereas Ubuntu's and Fedora's version of Firefox do not.
https://bugzilla.mozilla.org/show_bug.cgi?id=1610365#c4
It's important to remember that DoH or DNS over TLS does not provide you any tracking protection. Your ISP still knows every site you connect to. In fact, by using, someone else's DNS instead of your ISP's DNS, the only thing you have accomplished is to double the entities that can easily track your Internet activity - your ISP and now your DNS provider as well.
You may object and say with Devuan supporting Bonjour with mDNS (the automatic .local domain), there is no need to run a local DNS for local LAN devices. However, there are still many devices that do not support Bonjour with mDNS.
You may also object that most people do not run a local DNS. You would only be partially correct. Many people are running a DNS server but they don't know it. Many wireless router manufacturers, including such name brands as TP-Link are running a form of OpenWRT which means they are running dnsmasq which acts as both a DHCP server and a Dynamic DNS server. These routers allow you so select a local domain name in your router configuration. So, if you chose a local domain name of .lan and chose a Devuan box hostname of nosystemd, your router DNS would automatically assign your Devuan box a FQDN of nosystemd.lan. Unfortunately, many do not know that their wireless router has this capability and do not take advantage of it.
Offline
#12 2020-08-13 18:52:00
- Head_on_a_Stick
- Member

- From: London
- Registered: 2019-03-24
- Posts: 3,125
- Website
Re: HOWTO: Firefox DoH (DNS over HTTPS)
if you do that, you will be unable to do any local LAN-only domain DNS lookups
It will if a search line is added ![]()
Brianna Ghey — Rest In Power
Offline
#13 2020-08-13 20:30:50
- Vernon
- Member
- Registered: 2020-07-19
- Posts: 89
Re: HOWTO: Firefox DoH (DNS over HTTPS)
Vernon wrote:if you do that, you will be unable to do any local LAN-only domain DNS lookups
It will if a search line is added
No, a search directive does nothing but add a domain to a hostname with zero dots. It does not change DNS resolvers. As per your example /etc/resolv.conf file.
nameserver 9.9.9.9
search lanIf I try to ping printer, the search directive will only add .lan to the host name and change the hostname to printer.lan. Nameserver 9.9.9.9 will return NXDOMAIN because the .lan domain is only in my local DNS.
Offline
#14 2020-08-14 16:26:14
- chris2be8
- Member
- Registered: 2018-08-11
- Posts: 366
Re: HOWTO: Firefox DoH (DNS over HTTPS)
My approach is to put entries in /etc/hosts for local hardware. See the man page for hosts for details of how to format entries. This is quite manageable if you only have a few systems which all have fixed IP addresses (eg 1 router and 1 printer). And then use DNS for everything on the internet.
Chris
Offline
Pages: 1

