You are not logged in.
- Topics: Active | Unanswered
#1 2019-07-14 01:47:54
- alupoj
- Member

- Registered: 2019-01-25
- Posts: 80
Customizing Heads as a secure persistent guest for boards and VMs.
root@workstation:/etc/apt# apt update
Get:1 http://pkgmaster.devuan.org/merged beowulf InRelease [25.6 kB]
Get:2 http://pkgmaster.devuan.org/merged beowulf-updates InRelease [25.6 kB]
Get:3 http://pkgmaster.devuan.org/merged beowulf-security InRelease [25.6 kB]
Get:4 http://pkgmaster.devuan.org/devuan experimental InRelease [169 kB]
0% [1 InRelease gpgv 25.6 kB]gpgv: Signature made Sun Jul 7 01:30:05 2019 UTC
gpgv: using RSA key E032601B7CA10BC3EA53FA81BB23C00C61FC752C
gpgv: Good signature from "Devuan Repository (Amprolla3 on Nemesis) <repository@devuan.org>"
/usr/bin/apt-key: 624: /usr/bin/apt-key: cannot create /dev/null: Permission denied
E: Repository 'http://pkgmaster.devuan.org/merged beowulf InRelease' changed its 'Origin' value from '' to 'Devuan'
N: This must be accepted explicitly before updates for this repository can be applied. See apt-secure(8) manpage for details.
Do you want to accept these changes and continue updating from this repository? [y/N] y
terminate called after throwing an instance of 'std::runtime_error'
what(): random_device::random_device(const std::string&)
Aborted
Ran above in a chroot.
Further apt update executions do not show any messages anymore.
Now:
apt update
hangs forever until ^C.
Main system above chroot works fine with apt.
Tried to reproduce, the same thing after pressing Y as described above.
How can this be fixed?
Last edited by alupoj (2019-07-15 04:20:41)
Offline
#2 2019-07-14 03:45:07
- alupoj
- Member

- Registered: 2019-01-25
- Posts: 80
Re: Customizing Heads as a secure persistent guest for boards and VMs.
It is a Heads distro installation.
Fixed by manually (dpkg -i *deb) upgrading to versions from a newly bootstrapped directory.
Offline
#3 2019-07-14 15:12:27
- Panopticon
- Member
- Registered: 2018-01-27
- Posts: 306
Re: Customizing Heads as a secure persistent guest for boards and VMs.
It is a Heads distro installation.
Fixed by manually (dpkg -i *deb) upgrading to versions from a newly bootstrapped directory.
Do you mean you installed the Heads Live distro on persistent media? , how did you manage to do this?
Last edited by Panopticon (2019-07-14 15:12:40)
Offline
#4 2019-07-15 03:32:48
- alupoj
- Member

- Registered: 2019-01-25
- Posts: 80
Re: Customizing Heads as a secure persistent guest for boards and VMs.
At first I rsynced the OS to a virtual drive booted from a LiveCD in a virtual machine.
Then manually dpkg -i *.deb taken from the most recent debootstraped Beowulf.
Now able to boot my persistent (on guest ext3 over host zvol passed as a raw device) Heads in a KVM virtual machine from a host zvol but with another stock kernel.
Going to rewrite Heads initrd script to boot its grsec kernel from a virtual drive instead of a CD-ROM.
It will be a good start to distribute all my services over several (5-10 pieces) hardware motherboards like Via C3 ($5/board for used piece), Atom N270 ($10/board for used piece) and VPSes to avoid Spectre like attacks and CPU God mode activated from blobbed software like Skype or Chrome too. I am afraid such popular blobbed software may reflash controllers' firmwares to the most recent "trojaned editions".
Some boards will run this persistent Heads and a few of others will run OpenBSD.
Nothing helps today to prevent escalation to a root and escaping from a virtual machine when a single hardware machine is used for all programs and I guess there are still a lot of unknown surprises in the CPUs and other hardware.
So the only feasible solution to get a few better protection is to distribute all used services over several dedicated motherboards per service.
I am sure we will see many many new security flaws in new "fixed" CPUs just after 5-10 years passes since their release date, manufacturers will artificially make some researchers incidentally finding new exploits. It will stimulate to purchase even more newer CPUs even with a more intellectual backdoors and probes inside them.
And it is obvious all x86 CPUs have God mode like VIA C3.
Intel and AMD just made better work to hide root escalation backdoor from masses.
What to you think about ARM A7/A53 like Allwinner chips?
Do they have God mode too for root escalation?
Is it correct that all X86 CPUs are emulated like Bochs on a pure hardware processors with a RISC like architecture? Trasmeta, VIA and Elbrus at least stated is openly while Intel and AMD just do not mention it?
ARM A7/A53 are pure hardware chips, right? Do they have hardware backdoors except Trust World for a bootloaded trojan?
Btw, is there any method to easy verify Devuan public binaries are actually built from Devuan public sources? Is using Gentoo more secure in terms of avoiding unnoticed trojan injection into public Devuan binaries which we get over apt install?
If a deb is signed with Devuan PGP does it warrant a maintainer did not inject a trojan? I guess it does not warrant if maintainers does this intentionally. And what if their computers are infected by a trojan which injects trojan blob to compiled binaries when a maintainer does not do a harm by intention?
Is it a good idea to prefer Gentoo for small security specific hosts over Devuan (when OpenBSD is not suitable because of a different feature set compared to Linux or my unfamiliarity with OBSD)?
And then run Devuan only as rich application guests inside virtual machines inside a vm host like ascetic Gentoo (with a few of packages) and/or an ascetic OpenBSD (default packages)?
Last edited by alupoj (2019-07-15 04:48:28)
Offline
#5 2019-07-15 15:06:11
- Panopticon
- Member
- Registered: 2018-01-27
- Posts: 306
Re: Customizing Heads as a secure persistent guest for boards and VMs.
https://en.wikipedia.org/wiki/ARM_architecture
Hopefully the future of open source computing.
Offline
#6 2019-07-16 06:26:53
- alupoj
- Member

- Registered: 2019-01-25
- Posts: 80
Re: Customizing Heads as a secure persistent guest for boards and VMs.
https://en.wikipedia.org/wiki/ARM_architecture
Hopefully the future of open source computing.
Are there any affordable RISC-V boards running Linux and/or BSD on the public market?
Not micro controller boards with some specific non universal OS.
Last edited by alupoj (2019-07-16 06:27:48)
Offline
#7 2019-07-16 12:24:11
- Panopticon
- Member
- Registered: 2018-01-27
- Posts: 306
Re: Customizing Heads as a secure persistent guest for boards and VMs.
Panopticon wrote:https://en.wikipedia.org/wiki/ARM_architecture
Hopefully the future of open source computing.
Are there any affordable RISC-V boards running Linux and/or BSD on the public market?
Not micro controller boards with some specific non universal OS.
Not that i am aware of, but i haven't looked or researched it.
Offline
#8 2019-07-23 07:55:10
- alupoj
- Member

- Registered: 2019-01-25
- Posts: 80
Re: Customizing Heads as a secure persistent guest for boards and VMs.
Some progress on running Heads 32bit with its Libre grsec kernel from a persistent ZFS volume in KVM:
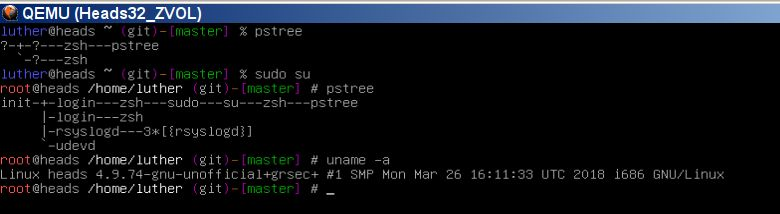
Graphical DE is temporary disabled.
Almost all permanently running services disabled.
Almost no running non kernel processes.
Installation can be used for making some routers like Whonix, automatic Torification/I2Pification, etc.
May be OpenBSD would be more secure, but unfortunately I am too newbie in OpenBSD ![]()
Most likely this kernel can run on a relatively old boards like VIA C3, Atom N270, etc.
So it can be used to distribute highly isolated services running on several (5-10) different hardware boards.
Goodbye Spectre and other CPU attacks on services by root escalation.
How to combine many boards in a single metal box?
Is it a good idea to power them by several PicoPSUs all connected to a single ATX PSU?
Are picoPSUs not backdoored yet? Say remotely powering off them by someones desire.
Last edited by alupoj (2019-07-23 08:24:05)
Offline
#9 2019-07-23 09:37:31
- alupoj
- Member

- Registered: 2019-01-25
- Posts: 80
Re: Customizing Heads as a secure persistent guest for boards and VMs.
May be it was better just to debootstrap a pure small Beowulf?
Ok, lets see how grsec works in Heads and will migrate the same idea to pure debootstrapped installation.
Offline
#10 2019-07-23 10:23:54
- alupoj
- Member

- Registered: 2019-01-25
- Posts: 80
Re: Customizing Heads as a secure persistent guest for boards and VMs.
Works fine even on P2 virtual CPU with 256M
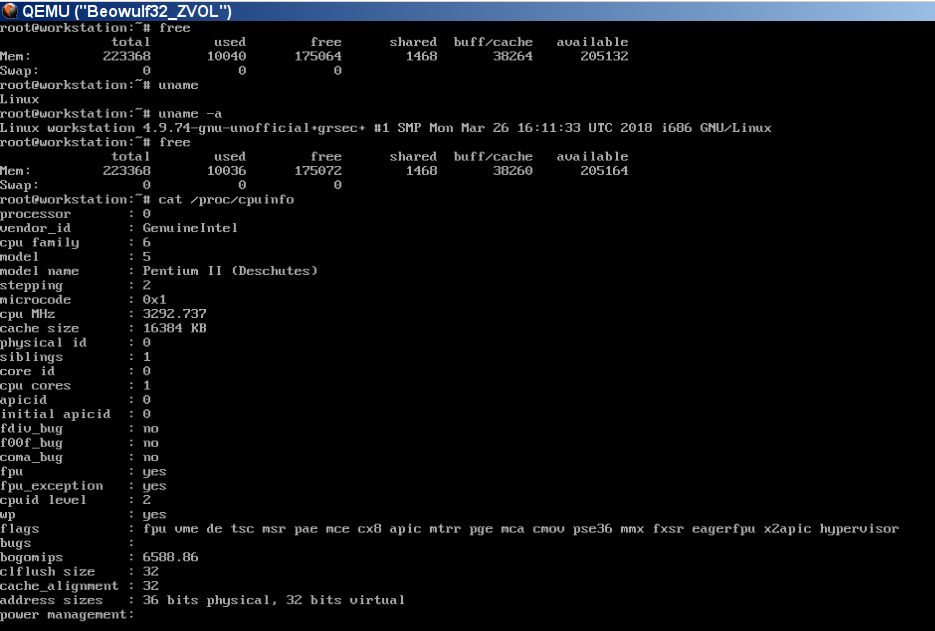
I guess my Thinkpad 770 will like this grseced Beowulf ![]()
dpkg -al | wc
only 253 packages installed yet.
Btw, does grsec work on older CPUs like P1 150 (not MMX) ?
May be just need to recompile the sources?
Last edited by alupoj (2019-07-23 10:26:42)
Offline
#11 2019-07-24 05:16:33
- alupoj
- Member

- Registered: 2019-01-25
- Posts: 80
Re: Customizing Heads as a secure persistent guest for boards and VMs.
Unfortunately i586 seems to be dropped in releases later than Jessie ![]()
Even if I build a kernel there are still no compatible prebuilt software packages, so Ascii, Beowulf, ..., etc. are useless for an old i586 I guess? Even i686 may be dropped in some next release.
So the only way to stay i586 notebook on an up to date Linux instead of OpenBSD is using Gentoo, right?
Slackware looks very buggy, even was not able to install LILO, when booted by GRUB i586 kernel panic occurred.
Gentoo mini installation ISO started even with i486 CPU, so Gentoo is a winner hands-down.
https://web.archive.org/save/http://yeo … eat-again/
Last edited by alupoj (2019-07-24 09:33:05)
Offline
#12 2019-07-25 04:56:14
- alupoj
- Member

- Registered: 2019-01-25
- Posts: 80
Re: Customizing Heads as a secure persistent guest for boards and VMs.
Well Gentoo with minipli-sources from Pentoo overlay seems to better suit my needs for a text only console on i486 than Devuan.
I thinks there are only a few Linux and BSD distros deserving someone's attention and time spent on their learning:
1) Devuan - like a current up to date old school Debian without ugly and nasty systemG, well suits for a desktop especially Trinity and for complex application servers, preferably open source like LAMP, PostgreSQL, etc., but not for blobbed enterprise like DB2 (though it is possible too). Good universal distro, very convenient, easy, reliable, predictable and fast to install, configure and update.
Devuan Ascii is very good to run with a deblobbed Libre kernel + ZFS rootfs + Trinity DE, exceptional quality and stability for any my task.
2) Gentoo - well suits for text only security tools on old or unusual hardware, very convenient to build anything from external sources in portages in third parties overlays, e.g. Pentoo. Easier to compile anything from Github than in Devuan especially for any desired architecture like i486. There is a very nice SystemRescueCd (even exists with integrated prebuilt ZFS) based on Gentoo, unfortunately now switched to ArchLinux, hopefully someone forks it to keep a Gentoo version too.
3) Centos - well suits for an enterprise server software like IBM DB2 DBMS or Microsoft SQL Server those install on Centos very smoothly. It is OK to run this monster with systemD in a well locked and hardened virtual machine, who cares, just works and third party enterprise software updates with less efforts on it. It is like a Linux version of Windows. You know it is idiotic to run Windows on a physical server, most likely Centos too ;b
On the other hand Centos' kernel is patched by was RedHat now IBM for stability, may be for some proprietary modern blobbed drivers, but do we need these anymore since we have clouds like Linode? Devuan is already more than enough for home servers with a relatively obsolete hardware. Current Centos requires systemD which is very bad of course.
4) NixOS - very convenient to do reproducible builds of software packages and even their installations with reproducible configurations. Good tool to experiment with many virtual machine guests running NixOS say in a cloud. Very bad it requires systemD as Centos does too, and no easy way to eliminate it.
Btw, there is also a GUIX Linux which is most likely a fork from NixOS and it does NOT use systemD which is very pleasant, not sure about more comparison details.
5) OpenBSD - Security winner, hands down. But very steep learning curve for an earlier Linux user taking into account there are no popular convenient tools even for listing device partitions like lsblk in Linux. Will learn it sometimes to use it on my routers and mail servers, not now yet. Hardened Gentoo will replace it for me for now as a good time saver hopefully unless hacked again by someones.
Why someone at enterprise would not create scripts to imitate Linux commands like lsblk on OpenBSD? I guess we would need just a few of dozens of commands (may be proxies to actual OpenBSD specific syntax) to make a comfortable introduction into the system for an earlier Linux admin. For example IBM DB2 DBMS has a compatibility layer for Oracle syntax, which is convenient to save time of developers when they migrate from Oracle DBMS to DB2, why not having something like this for migration of some servers from Linux to OpenBSD in terms of CLI commands syntax implemented as proxies to actual OpenBSD commands or APIs?
I do not see any practical need for other distros except for a diversity and a human right of freedom of choice and their creative work, IMHO all other universal Linux distributions are useless for my work unless based on above distros and/or provided like an overlay, e.g. Heads Linux, Exe Linux, Pentoo and SystemRescueCD.
Actually I would prefer features of Exe and Heads distros to be present in Devuan as packages: TrinityDE and GrSecurity kernel. And they shall not force users to upgrade versions, we need to be able to stay at old versions of Trinity as long as we need (like it is done in Devuan for example for ZFSonLinux versions now) unlike forced to migration to corrupted KDE v5 (hating it).
May be some other highly specialized distributions for example like for games, embedded, forensic works, etc. may have a sense too.
Last edited by alupoj (2019-08-12 05:27:58)
Offline

