You are not logged in.
- Topics: Active | Unanswered
#1 Re: ARM Builds » Devuan v9 for ARMv7 AllWinner - generic Libre kernel v5.3.1 » 2019-09-28 08:24:27
#2 Re: Installation » Please suggest how to get BBB running Devuan » 2019-08-20 11:28:34
Here's how u-boot is built for the devuan image: https://git.devuan.org/sdk/arm-sdk/blob … ack.sh#L63
I have two here, did not try them yet, but that's on my todo list, so if you need halp I can spend some time on it
but basically you should make an SD card with two partitions, one fat32 of a few Mo, with 5 files :
MLO : a reduced version of u-boot, which fits in the CPU instruction cache (128k), and which MUST have the name MLO
u-boot.img : full version of u-boot
uEnv.txt : environnement for the full version of u-boot
zImage : linux kernel
am335x-boneblack.dtb : device tree for the linux kernel
the names of the last four files depends on the configuration you have in the MLO, u-boot and uEnv.txt
You can find the files in this archive : http://www.nathael.org/Data/Devel/BBB/r … 4.1.tar.xz
in the same directory you also have base images for the rootfs to be extracted on the second partition of the SD card
and the patched sources for both u-boot and linux kernel
IF you rather want to do it on your own, then you can follow instructions from here : http://www.nathael.org/wiki_cpe/index.php/Dev/BBB
these are in french, but I think that a google translate whould do the job ... though there is very little text to translate.
the difference between the cross-compilation toolchains gcc-arm-none-eabi, gcc-arm-linux-gnueabi and gcc-arm-linux-gnueabihf are :
none vs linux : none targets micro-controllers and thus includes no libc, while linux targets linux systems, whith a libc
gnu : targets GNU libc
eabi vs eabihf : eabi is for ARM processors without a FPU (debian armel architecture), while eabihf targets those with a FPU (hardfloat) (debian armhf architecture)
you can also have gcc-arm-linux-uclib
which uses the uClibc instead of the GNU libc
the name is in the form "gcc-architecture-OS-libc"
whith some addition of the ABI used for ARM and MIPS toolchains where there can be many of them (mips is much worse than ARM for the ABI part)
apt-cache search gcc mips ...
boot.scr is not like a grub "stage 2"
it's an u-boot script
it is converted from boot.cmd using this command : mkimage -C none -A arm -T script -d boot.cmd boot.scr
which only adds a header to the boot.cmd file for u-boot
it has the same role as the uEnv.txt file for the beaglebone, and the name is specified in the u-boot configuration when u-boot is compiled
the support for text files with or without the header is also an u-boot configuration option
and you can create a system which needs no such configuration file, as u-boot can embed a default config, so once you know what you want, you can put it in the default u-boot config and get rid of the text file
same for the second u-boot on both beaglebone and allwinner boards
the first one (MLO for beaglebone or spl.bin for allwinner) is a simplified u-boot which can run in the processor instruction cache and data cache, which thus needs to be small enough, and which job is to init the DDR and start a second u-boot which in turns loads the linux kernel
the need for two u-boot is only beacause a full-featured u-boot does not fit in the instruction cache
needs to be less than 32k or something like that, right?
but once you know what you need, you can keep only the required parts in the first u-boot and tell it to load you kernel instead of the second u-boot
the size depends on the processor
under 128k for the AM335x of the beaglebone
I did not check for the Allwinner H2+ of the OrangePi zero
hum, the spl is indeed very small (18k) so the limit may be lower for the Allwinner H2+
i do remember getting that impression from elsewhere before
yep, from the H2+ documentation, 32k L1 instruction cache
this is very processor specific
it might be harder to get enough in the first stage u-boot (spl) to run the Linux kernelQ: please let me know, where can I find BROM description?
does it always try to boot from SD at first?
A: the details of bootrom behaviour can be found in the AM335x Technical Reference Manual, but the short answer is: on the BBB by default bootrom checks { eMMC, μSD, uart0 (xmodem), usb0 (rndis } in that orderQ: how can I boot from SD if something bootable is present on the eMMC?
A: if you power on with the S2 button (aka the boot mode button) held down then the boot order (for bootrom) becomes { SPI flash, μSD, usb0 (rndis), uart0 (xmodem) }
you can (and should) let go of the S2 button once the power led turns on (or to be technical, 20 milliseconds after the power led turns on)
there is no SPI flash on beaglebones (except the BeagleBone Enhanced if I remember correctly) but you're free to connect one if you have some reason for it
note that this only determines where bootrom looks for u-boot (or rather, the MLO which contains the u-boot SPL), u-boot typically makes its own decisions with regard to where to load linux fromQ: thanks for letting me know
SPI flash is an additional storage option? it is connected to some pins?
A: angstrom has not been the default for many, many years. this was before I started using beaglebones so I don't know anything about itQ: are uboot and kernel bound to each another somehow?
A: nope, in general they are not, however it is recommended to use the u-boot that came with whatever image you want to use
u-boot = x86 bios + grub...
in theory, but in practice there can still be trouble... for example, current debian images normally use u-boot overlays, but this isn't supported by old u-boot versionsQ:then what BROM is?
a very basic bios that you have no control other then 16/8 gpio..
does not BROM do hardware initialization like DDR?
A: nopeQ: is it reflashable? is there a source for BBB BROM somewhere?
A: bootrom is hard-baked into the SoC basically just does very rudimentary setup of the processor and loads the next stage into the internal SRAM. it will not do any board-specific setup such as DDR memoryQ:how can I be sure there is no a trojan for TrustZone?
A: you can't, but trustzone is not really supported anyway (technically there's a secure monitor, but it is only used to handle a small number of Secure Monitor Calls used to write to special registers that are not directly writable by the OS)
there's no secure-world kernel on AM335x GP devicesQ: Cortex A8 is stated to have a TrusZone? Is TI version any different?
A: I feel like I literally just answered thatQ: it means BBB CPU does not meet Cortex A8 specs?
A: it's r2p1 Cortex-A8 with neon...
and I feel like you're asking questions about things you don't really understand yet yourself
thumb2 works unlike the r1p3's we used on the Beagle/xM
also, I think it's r3p2Q: sorry, I even do not know what r2p1 is, are these revisions?
A:yep, definitely r3p2,
yes, cortex-a8 revisions
r3p2 is the last revision
anyway, the short summary is: even though the cortex-a8 core itself has trustzone support, it is not usable on GP versions of the AM335x, which is what's used on the BBBQ: can you please point me to a public explanation of this interesting issue related to TrustZone being revision specific for a Cortex A8 CPU?
A: support@ti.com can help you.
except for a tiny bit of initialization after reset and a tiny SMC handler, everything on the BBB runs in public (aka "non-secure") world
has nothing to do with the cortex-a8
it's just how it's setup on the AM335xQ: may be TZ is just not usable by end users but still usable by a trojan injected on the factory?
A: if you want to be able to trust hardware, you'll have to design your own processor and create it by soldering transistors together
have funQ: haha, very smart, I still can choose AllWinner
A: lol, I'd trust a TI SoC a lot more than an AllWinner one
lol, and your worried about TI's trojans'!!! China already back-doored that one..
I'm not concerned about trustzone on the BBB... if somewhere were going on in secure world, that would be observable anywayQ: there is known method for a root escalation in AllWinner, but for a client mode it does not matter
I would prefer something with backdoors but without already injected active trojans
A: also, it's hard to imagine what that trojan could do, given that it only has 1KB of ram that's private to secure worldQ: is not all RAM related to TZ not readable from outside?
A: there's reason to believe TI would put a trojan in their hardware... it would be easy to discover and cause terrible damage to their reputationQ: unless they are forced to do so by NSA or by above regulations
"RAM related to TZ" is meaningless... trustzone doesn't specify anything about RAM
otherwise no way to a public market?
for all things trustzone: https://developer.arm.com/ip-products/s … /trustzone
you just seem really paranoid about a topic you know very little about
trustzone is irrelevant on the BBB
sounds good, though hardly believable
A:what you do or do not believe is not my problem
sure, thank you very much for your earlier suggestionsQ:does a lack of TZ depend on BBB release year or revision
besides, DEFCON was last week, nothing is "secure" today, till all the things pointed out is fixed.
A:but I'm pretty security-paranoid myself, have dug a fair bit into bootrom on the AM335x, have dumped and partially reverse-engineerd the secure part of bootrom on the DM814x (a direct ancestor of the AM335x) to see what it does
based on all that, my opinion is: there's no need to worry about bootrom
all 1Ghz Aam335x are the same die revision..
no, it applies to all AM335x SoCs, and I think all TI SoCs in general (except maybe the latest ones, I don't know much about those yet)Q: it looks like a BBB much better in terms of security than X86?
A: X86 is horrible, though BBB isn't secure.. it wasn't designed for that.. it was designed for usablity..Q: cannot DMA be isolated by software on X86?
A: it's only isolated if you dump a bucket of cement on it and throw it into the ocean..A: Regarding OpenBSD, it's easier then that.. While testing efi boot, i noticed u-boto doesn't scrub memory, hence if you reboot, and halt.. EVERYTHING is still in DDR3
Q:grsec pax is known to protect from unknown errors in code
does not grsec 4.9 do it better than linux v5x?
A:anything worth a damn was already implemented by kees and pushed into mainline.
#3 Re: Installation » Please suggest how to get BBB running Devuan » 2019-08-15 01:47:20
I have found there is SDK to build ARM images for different supported boards:
https://git.devuan.org/sdk/arm-sdk
After reading corresponding script:
https://git.devuan.org/sdk/arm-sdk/blob … ack.sh#L63
I am still not sure, what is rebuilt from source in it except kernel? Uboot?
All userspace is debootstrapped in a precompiled binary form from corresponding Devuan repository?
How to rebuild the whole installation from source like Gentoo?
Preferably by cross compiling on a X86 host or at least via distcc helper.
Can you please include those options for a full rebuild from source into the SDK?
#4 Re: Installation » Please suggest how to get BBB running Devuan » 2019-08-14 04:29:09
I mounted the image:
/dev/loop0p1 on /mnt/d1 type vfat (rw,relatime,fmask=0022,dmask=0022,codepage=437,iocharset=iso8859-1,shortname=mixed,errors=remount-ro)
/dev/loop0p2 on /mnt/d2 type ext4 (rw,relatime)First one is a boot loader and second is root fs.
I was suggested uboot is flashed into beginning sectors of the media from which BBB boots from its BROM.
#5 Installation » Please suggest how to get BBB running Devuan » 2019-08-14 03:54:00
- alupoj
- Replies: 4
Dear Friends,
There are a lot of manuals with a lot of undesirable time waste information how to flash Beaglebone Black, e.g.:
https://beagleboard.org/getting-started
The first what I have read of course is:
https://files.devuan.org/devuan_jessie/ … README.txt
It is clear I have to dd image to SD, it is easy.
How can I replace uboot and kernel?
I do NOT see an uboot bin for the BBB:
https://devuan.4isp.it/devuan_ascii/embedded/u-boot/
May I build my own kernel in Gentoo in cross compiling mode and place it to BBB?
Will grsec minipli kernel work fine on this board with Devuan?
Does there exist an RT grsec kernel source? Can RT and grsec be mixed at all?
Can grsec+deblobbed+RT kernel be run on BBB? Is RT kernel less secure than non RT or it does not matter?
Can I use XFS as a root FS for the installation? Or is it too much memory hungry for a 512Mb board? and may be even not compatible with grsec?
Thank you for your help, it is very valuable.
#6 Re: Installation » Customizing Heads as a secure persistent guest for boards and VMs. » 2019-07-25 04:56:14
Well Gentoo with minipli-sources from Pentoo overlay seems to better suit my needs for a text only console on i486 than Devuan.
I thinks there are only a few Linux and BSD distros deserving someone's attention and time spent on their learning:
1) Devuan - like a current up to date old school Debian without ugly and nasty systemG, well suits for a desktop especially Trinity and for complex application servers, preferably open source like LAMP, PostgreSQL, etc., but not for blobbed enterprise like DB2 (though it is possible too). Good universal distro, very convenient, easy, reliable, predictable and fast to install, configure and update.
Devuan Ascii is very good to run with a deblobbed Libre kernel + ZFS rootfs + Trinity DE, exceptional quality and stability for any my task.
2) Gentoo - well suits for text only security tools on old or unusual hardware, very convenient to build anything from external sources in portages in third parties overlays, e.g. Pentoo. Easier to compile anything from Github than in Devuan especially for any desired architecture like i486. There is a very nice SystemRescueCd (even exists with integrated prebuilt ZFS) based on Gentoo, unfortunately now switched to ArchLinux, hopefully someone forks it to keep a Gentoo version too.
3) Centos - well suits for an enterprise server software like IBM DB2 DBMS or Microsoft SQL Server those install on Centos very smoothly. It is OK to run this monster with systemD in a well locked and hardened virtual machine, who cares, just works and third party enterprise software updates with less efforts on it. It is like a Linux version of Windows. You know it is idiotic to run Windows on a physical server, most likely Centos too ;b
On the other hand Centos' kernel is patched by was RedHat now IBM for stability, may be for some proprietary modern blobbed drivers, but do we need these anymore since we have clouds like Linode? Devuan is already more than enough for home servers with a relatively obsolete hardware. Current Centos requires systemD which is very bad of course.
4) NixOS - very convenient to do reproducible builds of software packages and even their installations with reproducible configurations. Good tool to experiment with many virtual machine guests running NixOS say in a cloud. Very bad it requires systemD as Centos does too, and no easy way to eliminate it.
Btw, there is also a GUIX Linux which is most likely a fork from NixOS and it does NOT use systemD which is very pleasant, not sure about more comparison details.
5) OpenBSD - Security winner, hands down. But very steep learning curve for an earlier Linux user taking into account there are no popular convenient tools even for listing device partitions like lsblk in Linux. Will learn it sometimes to use it on my routers and mail servers, not now yet. Hardened Gentoo will replace it for me for now as a good time saver hopefully unless hacked again by someones.
Why someone at enterprise would not create scripts to imitate Linux commands like lsblk on OpenBSD? I guess we would need just a few of dozens of commands (may be proxies to actual OpenBSD specific syntax) to make a comfortable introduction into the system for an earlier Linux admin. For example IBM DB2 DBMS has a compatibility layer for Oracle syntax, which is convenient to save time of developers when they migrate from Oracle DBMS to DB2, why not having something like this for migration of some servers from Linux to OpenBSD in terms of CLI commands syntax implemented as proxies to actual OpenBSD commands or APIs?
I do not see any practical need for other distros except for a diversity and a human right of freedom of choice and their creative work, IMHO all other universal Linux distributions are useless for my work unless based on above distros and/or provided like an overlay, e.g. Heads Linux, Exe Linux, Pentoo and SystemRescueCD.
Actually I would prefer features of Exe and Heads distros to be present in Devuan as packages: TrinityDE and GrSecurity kernel. And they shall not force users to upgrade versions, we need to be able to stay at old versions of Trinity as long as we need (like it is done in Devuan for example for ZFSonLinux versions now) unlike forced to migration to corrupted KDE v5 (hating it).
May be some other highly specialized distributions for example like for games, embedded, forensic works, etc. may have a sense too.
#7 Re: Installation » Customizing Heads as a secure persistent guest for boards and VMs. » 2019-07-24 05:16:33
Unfortunately i586 seems to be dropped in releases later than Jessie ![]()
Even if I build a kernel there are still no compatible prebuilt software packages, so Ascii, Beowulf, ..., etc. are useless for an old i586 I guess? Even i686 may be dropped in some next release.
So the only way to stay i586 notebook on an up to date Linux instead of OpenBSD is using Gentoo, right?
Slackware looks very buggy, even was not able to install LILO, when booted by GRUB i586 kernel panic occurred.
Gentoo mini installation ISO started even with i486 CPU, so Gentoo is a winner hands-down.
#8 Re: Installation » Customizing Heads as a secure persistent guest for boards and VMs. » 2019-07-23 10:23:54
Works fine even on P2 virtual CPU with 256M
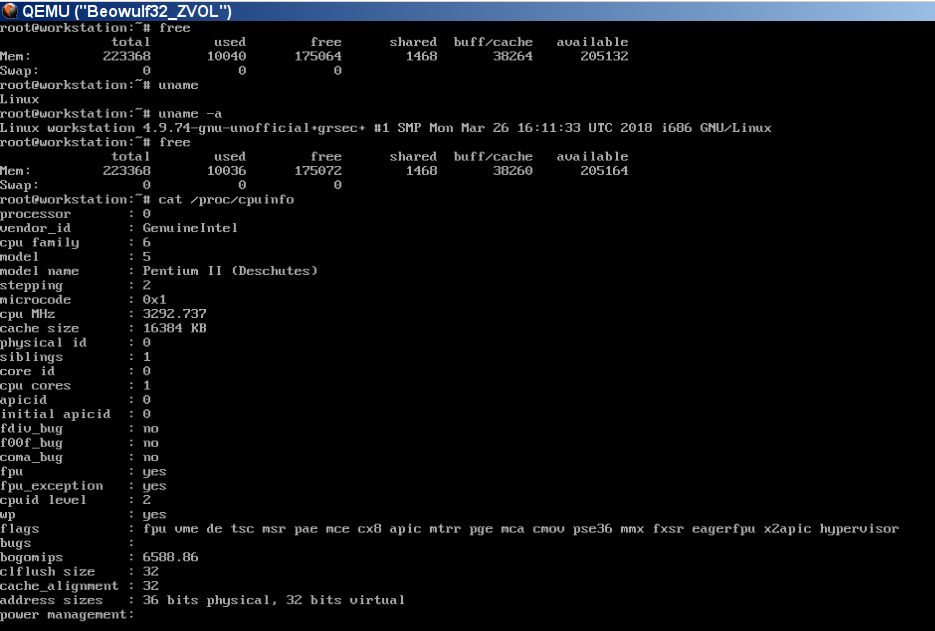
I guess my Thinkpad 770 will like this grseced Beowulf ![]()
dpkg -al | wc
only 253 packages installed yet.
Btw, does grsec work on older CPUs like P1 150 (not MMX) ?
May be just need to recompile the sources?
#9 Re: Installation » Customizing Heads as a secure persistent guest for boards and VMs. » 2019-07-23 09:37:31
May be it was better just to debootstrap a pure small Beowulf?
Ok, lets see how grsec works in Heads and will migrate the same idea to pure debootstrapped installation.
#10 Re: Installation » Customizing Heads as a secure persistent guest for boards and VMs. » 2019-07-23 07:55:10
Some progress on running Heads 32bit with its Libre grsec kernel from a persistent ZFS volume in KVM:
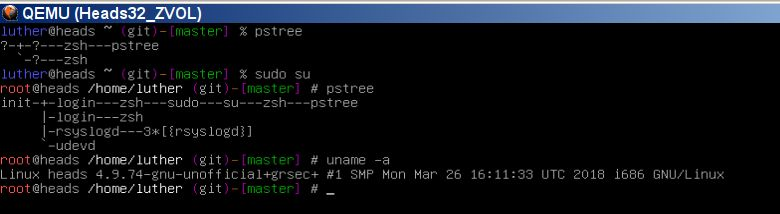
Graphical DE is temporary disabled.
Almost all permanently running services disabled.
Almost no running non kernel processes.
Installation can be used for making some routers like Whonix, automatic Torification/I2Pification, etc.
May be OpenBSD would be more secure, but unfortunately I am too newbie in OpenBSD ![]()
Most likely this kernel can run on a relatively old boards like VIA C3, Atom N270, etc.
So it can be used to distribute highly isolated services running on several (5-10) different hardware boards.
Goodbye Spectre and other CPU attacks on services by root escalation.
How to combine many boards in a single metal box?
Is it a good idea to power them by several PicoPSUs all connected to a single ATX PSU?
Are picoPSUs not backdoored yet? Say remotely powering off them by someones desire.
#11 Re: Off-topic » Please suggest a completely open source ARM board with Cortex A53/A7 » 2019-07-20 22:23:28
No.
Can you please explain in more details why no?
How a SATA firmware on HostB (in a disk controller or disk) can influence HostA if I have a chain like this:
HostA ZFS over local LUKS (cryptsetup) -> iSCSI over Ethernet -> HostB -> SATA -> Disk
What HostB can do bad to HostA RAM? Does it have any access to HostA RAM?
The only bad thing seems to be just damaging data on the disk by the disk itself? But it will be instantly indicated by ZFS on HostA.
If iSCSI is not secure enough we still have many other network block and file protocols even like SSHFS,
and still no?
#12 Re: Off-topic » Please suggest a completely open source ARM board with Cortex A53/A7 » 2019-07-20 09:36:46
ToxicExMachina wrote:If you want affordable computer with blobless firmware - go buy Thinkpad T60 and flash libreboot.
The hard drive controller in that machine contains embedded firmware which is powerful enough to pwn the device.
Would iSCSI or NFS help if using such a chain of connection to disks:
T60 -> iSCSI (IP over Ethernet) -> OrangePI -> SATA
?
#13 Re: Off-topic » Please suggest a completely open source ARM board with Cortex A53/A7 » 2019-07-20 06:23:59
2. Older ARM versions - older than modern ARM.
Please recommend an example of such an ARM board.
#14 Re: Off-topic » Please suggest a completely open source ARM board with Cortex A53/A7 » 2019-07-20 06:20:51
alupoj wrote:ToxicExMachina wrote:BIOS is opensource: https://www.seabios.org/
UEFI is also opensource: https://www.tianocore.org/SeaBIOS originally looks like a BIOS for virtual machine guests.
Can SeaBIOS be used directly on any physical motherboard without Coreboot hack which I already mentioned?
Is not SeaBIOS just one of many other possible payloads like GRUB or KEXEC, etc. for Coreboot/Libreboot?Where would be SeaBIOS without Coreboot/Libreboot projects which actually are apposite of what was intended for "openness" (actually lack of openness) of X86 boot loader?
It doesn't matter. Every vendor had own BIOS implementation because it totally depends on hardware by design. BIOS is a part of MS-DOS designed to provide abstraction layer for compatibility purposes. SeaBIOS is another implementation. In this case Coreboot+SeaBIOS == BIOS.
The problem with X86 BIOS as already mentioned earlier is the whole thing about X86 initialization process is proprietary unlike ARM where initialization of several popular (not all boards of course, especially proprietary are Mobile ARMs) development single boards is documented and even with an official open source uboot.
#15 Re: Off-topic » Please suggest a completely open source ARM board with Cortex A53/A7 » 2019-07-20 06:16:35
alupoj wrote:While Raptor motherboard is probably free of proprietary blobs, the POWER9 CPU is most likely not?
And all of them are not affordable for me.If you want affordable computer with blobless firmware - go buy Thinkpad T60 and flash libreboot.
I have it, but CPU itself does not seem to be trustworthy.
IMHO Pentium 1 + OpenBSD looks more interesting even without Libreboot. I have a couple of them too, just wonder how to combine all these things together to produce a more secure working place.
Anyway all DMA extension boards shall be moved to another host and connected via IP to avoid DMA attacks from firmwares of attached devices like SATA storage, USB dongles, PCI expansion cards, etc.
#16 Re: Off-topic » Mate and Trinity » 2019-07-20 01:02:19
A few months ago several times I experienced my KDE destroyed knotes and kalarm records at the most inconvenient moment of time for me, most likely remotely by someone spying.
So I lost important ideas and notices, a few of plans and appointments.
KDE became suspicious after moving knotes and kalarm data into a database instead of old plain files, it is even KDE v4, I tried KDE v5 and rolled back system ZFS partition at once as it looks ugly and unusable for me.
After moving to Trinity it does not happen anymore.
After some configuration Trinity looks like the most pleasant DE I have ever seen yet.
Very sad if its technical design is attacked sometimes by the same morons who damaged original KDE.
IMHO two the most significant corruptions happened to open source during a few last years are:
1) Debian became a systemd only distro
2) KDE became a spying and invading environment not caring about user time, like a tool for remote internet ganstalkers targeting the user of KDE installation.
Both these software corruptions happened hardly noticeable almost invisible during relatively smooth apt upgrades and I had to move too late (in terms of my wasted time) already when it became absolutely impossible to suffer corruptions.
I hope if Devuan and Trinity get corrupted sometimes they will be forked again and invaders will be off the pure board finally.
#17 Re: Off-topic » Please suggest a completely open source ARM board with Cortex A53/A7 » 2019-07-19 18:04:21
The POWER9 microarchitecture is open source and Raptor's offerings are blob-free but it's aimed at high TPD servers rather than low power hacker boards.
While Raptor motherboard is probably free of proprietary blobs, the POWER9 CPU is most likely not?
And all of them are not affordable for me.
#18 Re: Off-topic » Please suggest a completely open source ARM board with Cortex A53/A7 » 2019-07-19 15:50:42
Enough of the loony tunes, This is a board forum about the Devuan operating system, not x86 god mode. Go away
You are wrong. This area is an offtopic for Devuan and therefore non offtopic (ontopic) for anything else for example like CPU backdoors.
I would prefer you to go away from my rightful and correct thread in this offtopic for Devuan area.
#19 Re: Off-topic » Please suggest a completely open source ARM board with Cortex A53/A7 » 2019-07-19 13:40:18
It's not criteria of open source. Microcode is conception from the middle of XX century.
Uhaha, who cares which century from a conception of X86 microcode is if it's current implementation is TOP SECRET proprietary with integrated NSA backdoors and trojans.
#20 Re: Off-topic » What other distro are you using (besides devuan)? » 2019-07-18 23:39:08
What to you think about Gentoo being more secure than Devuan for small installations like a text mode only computers?
#21 Re: Off-topic » Please suggest a completely open source ARM board with Cortex A53/A7 » 2019-07-18 23:20:42
You seem to be obsessed with "open source evarything', assuming because you "have reservations" about people trying to spy on you. That's fine, but if you're that paranoid about privacy, don't use a computer you haven't build from scratch yourself! Design your own hardware, using Open Source is quite easy: Kicad. Make your own PCB's, now that's a challenge if you know nowt about electronics. For chips, use un-programmed FPGA's. Not exactly open source, but as the specific chips in your system cannot be identified at the time of manufacturing, there's little risk you're targeted via this route (s'cuse the pun) Write your own bootloader, booting a plain, but patched (by yourself) Linux kernel. Next, create the entire ecosystem for your desktop, or rely on GNU/Hurd to port their software to your specific hardware. Not impossible, but quite unrealistic.
Maybe you should try being less paranoid about privacy, it's healthier too
PS: the suggestion to learn more about what certain phrases mean in FLOSS-land is highly recommended.
Most likely you know, personal time is the most valuable resource which is hard or impossible to restore.
You are trolling like a ganstalker from some 3 letter agency just to waster target life. Also I am not interested to self develop in any area out of my specialization and hardware design is out of my scope for sure.
Building own PC is not a way to go for me for sure, I am just looking for different ready solutions and possibilities to combine them.
For example: Pentium 1 computer from 1997 running modern OpenBSD with 16 bit Ethernet card without DMA connecting to a Cortex A7 single board like Orange PI which has a USB and Linux for connecting Nitrokey looks more realistic than your fancies about self make DIYs.
Pentium1+OpenBSD -> 16bit Ethernet PCMCIA -> OrangePI+Gentoo->Nitrokey
How about this?
Are obsolete P1 backdoors old enough to prevent active invasion into my LAN?
There are still many other variants to try for a more secure textual console like for example 8bit ZX spectrum.
#22 Re: Off-topic » Please suggest a completely open source ARM board with Cortex A53/A7 » 2019-07-18 11:40:24
x86 has own firmware standard. Initially it was BIOS. Now it's UEFI instead of BIOS. There are mostly same hotkeys, 99% same boot mechanism for motherboards from totally different vendors. At the same time every ARM board (even development boards) has own uboot fork, own bugs, own BSP kit incompatible with others, etc. There are enough powerful ARM workstations even today - see ThunderX based computers. The result is still same: proprietary platform. The only advantage is a lot of devices with ultra low power consumption. That's all ARM has. Some terrible things came to x86 from ARM. For example, AMD PSP is just an ARM TrustZone implementation.
I agree with you that X86 standard is versatile and open for vendors to produce X86 hardware, but is the most unfriendly for people who would like to write their own open source boot loader, that is what I primary meant under open source. And Olinuxino makers provide even open source schematics, do not they?
#23 Re: Off-topic » Please suggest a completely open source ARM board with Cortex A53/A7 » 2019-07-18 11:30:29
It's not criteria of open source. Microcode is conception from the middle of XX century.
I primarily was looking for an affordable board with an open source boot loader.
And preferably if its CPU would not have backdoors or at least a virtualized spying trojan.
I thought PSP is an additional processor out of user control but with complete access to user's computer including RAM. While TrustZone is just a CPU feature able to create highly isolated execution environment for some earlier loaded program (spying trojan too, but on the same CPU)?
And who knows how long ago PSP appeared in AMD CPUs? May be since Duron?
How TrustZone is related to AMD PSP?
Though according to this article, they are similar, need to read it yet.
Well, though PSP is a dedicated ARM processor, it does not make a sense to compare TrustZone itself to a dedicated spying ARM coCPU (which lets has its own TrustZone, but who cares).
#24 Re: Off-topic » Please suggest a completely open source ARM board with Cortex A53/A7 » 2019-07-18 11:22:14
BIOS is opensource: https://www.seabios.org/
UEFI is also opensource: https://www.tianocore.org/
SeaBIOS originally looks like a BIOS for virtual machine guests.
Can SeaBIOS be used directly on any physical motherboard without Coreboot hack which I already mentioned?
Is not SeaBIOS just one of many other possible payloads like GRUB or KEXEC, etc. for Coreboot/Libreboot?
Where would be SeaBIOS without Coreboot/Libreboot projects which actually are apposite of what was intended for "openness" (actually lack of openness) of X86 boot loader?
#25 Re: Off-topic » Please suggest a completely open source ARM board with Cortex A53/A7 » 2019-07-18 11:16:24
different MIPS cores
Can routers running LibreCMC be treated more secure in terms of my control over their boot loader?


